Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium

Small 75u sample from my first bubble hash attempt. Used a freezer and a microplane. My buddy was in the stars last night so I guess it turned out okay. : BubbleHash

2: A simple depiction of the user authentication process. Evil Eve is... | Download Scientific Diagram

Our hash is showing up at more and more retailers! Any guess from this picture where we just replenished supply? | Bubbles, Hashing




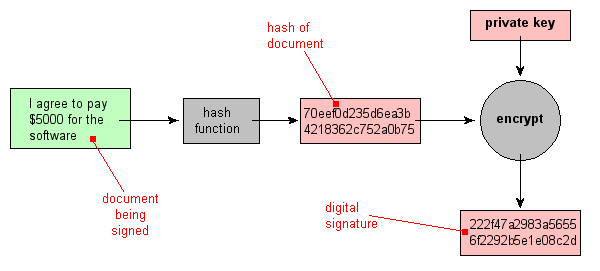




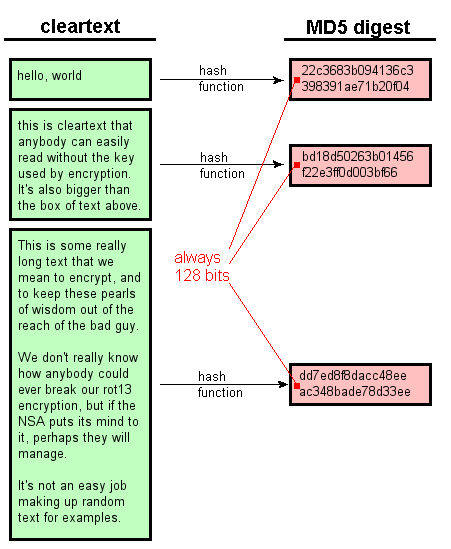





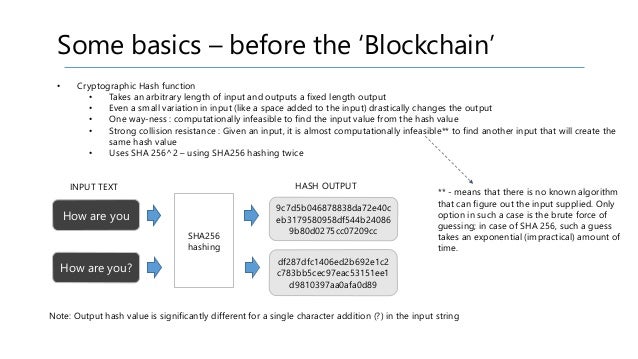

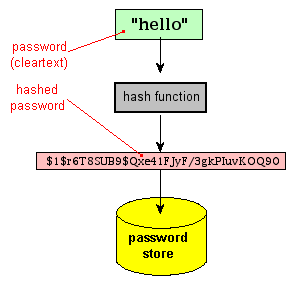
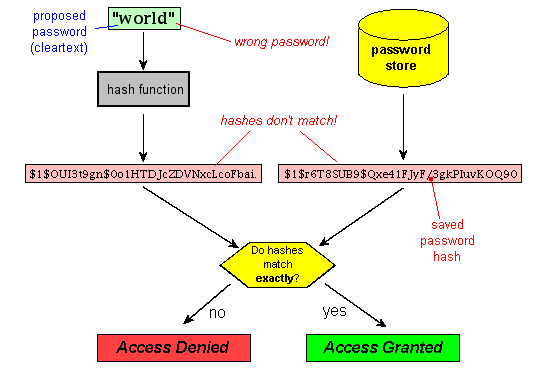



![What Is Cryptographic Hash? [a Beginner's Guide] What Is Cryptographic Hash? [a Beginner's Guide]](https://techjury.net/wp-content/uploads/2020/06/hash-functions-speed-1024x753.png)